The RPC Portmapper Service is a service which ensures that certain applications end up at the right port. This is used, for example, for NFS / fileserver applications. Unfortunately, in the case of external access, this service can be abused as a 'reflector' / 'amplification' in order to contribute to a (D)DoS attack. Therefore, it is important that you disable this service or make it unreachable for external access.
How to make the remote access service unreachable can be found below for the most used firewalls:
Use sudo or a root user when following the steps in this article
Disabling the service
Disabling the portmapper service altogether is one of the most secure messures you can take. How you disable the service differs per OS, but in most cases, you can disable the portmapper service using the following commands:
systemctl stop rpcbind
systemctl stop rpcbind.socket
systemctl disable rpcbind
systemctl disable rpcbind.socketThe firewall in your control panel
In het TransIP control panel offers a free firewall for all your VPSs. If you enable this firewall, all incoming ports, including port 111, are blocked automatically and your VPS will no longer be vulnerable.
You decide then which ports are available for incoming traffic on your VPS. In our VPS-Firewall documentation we explain using the firewall in more detail.
Firewalld (CentOS 7, DirectAdmin, Plesk, cPanel)
In Firewalld you can close port 111 (used by portmapper) by simply removing it from the open ports (Plesk uses --zone=plesk):
firewall-cmd --permanent --zone=public --remove-port=111/udp
You will then see "success" as feedback on the command line. When this is saved, you then reload the firewall for the new rule to take effect:
firewall-cmd --reloadPlease note! It is possible that you use a 'private' firewall so these commands do not work. This is the case, for example, when you use Plesk (here, you can close the ports via Tools & Settings > Firewall) or use an application such as ConfigServer Security & Firewall (CSF). You can, for example, also install and enable IPtables on CentOS 7 instead of firewalld. Check this first before you execute these commands.
Do you actually need the RPC-portmapper service because you're hosting a fileserver application and another server/computer requires access to it? In that case, only allow port 111 for the IP belonging to this server/computer using the command below, where 123.123.123.123 should be replaced by the IP address belonging to the server that requiress access.
firewall-cmd --permanent --zone=public --add-rich-rule='UFW (Ubuntu / Debian)
UFW is the default firewall for Ubuntu & Debian. You can close port 111 using the command:
ufw deny 111Do you actually need the RPC-portmapper service because you're hosting a fileserver application and another server/computer requires access to it? In that case, only allow port 111 for the IP belonging to this server/computer using the command below, where 123.123.123.123 should be replaced by the IP address belonging to the server that requiress access.
ufw allow from 123.123.123.123 to any port 111 proto udpIPtables
If you use IPtables, you can close the relevant port with the following command:
iptables -A INPUT -p udp --dport 111 -j DROP
Here too you will then have to 'reload' the firewall to activate the new rule:
iptables-save | sudo tee /etc/sysconfig/iptables service iptables restart
Please note! If you use Debian, iptables will not run as a service by default (see also the following article). In that case, you can choose to enable this via the command "apt-get install iptables-persistent".
Windows Server Firewall
The steps below are relevant for blocking the portmapper port in Windows Server 2008, 2012, 2016 & 2019.
Step 1
Click the start button and use the search term 'Firewall'. Alternatively, you can also find the firewall in the Server Manager under 'Tools'.
Among the search results, 'Windows Firewall with Advanced Security' will appear. Click it.
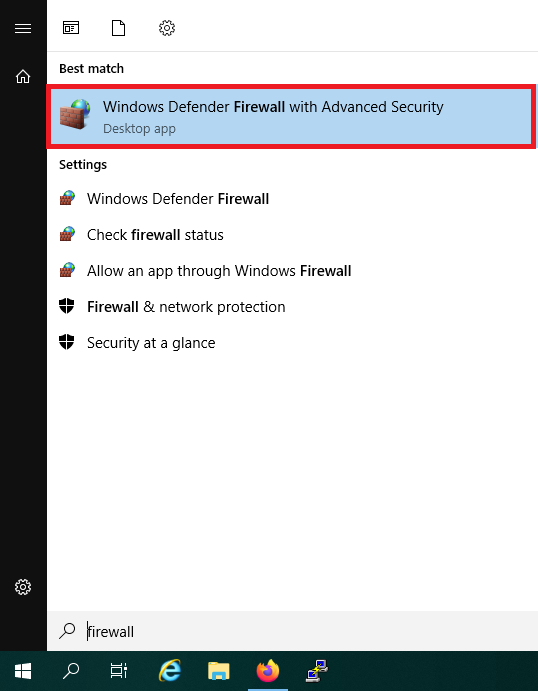
Step 2
Navigate to 'Inbound Rules', right click 'Inbound Rules' and choose 'New Rule'.
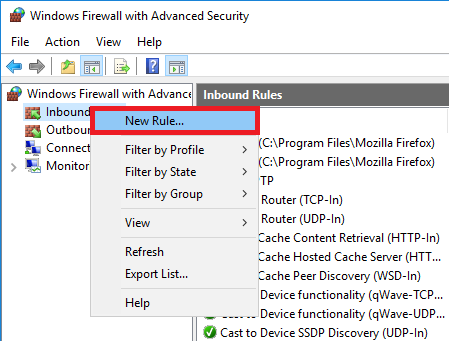
Step 3
Select: 'Port' and click 'Next'.
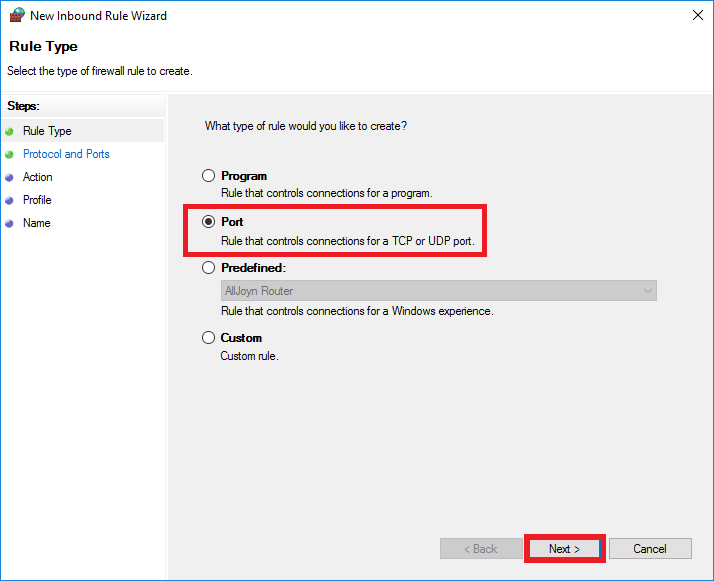
Step 4
Select 'UDP' and enter '111' at 'Specific local ports'. Then click 'Next'.
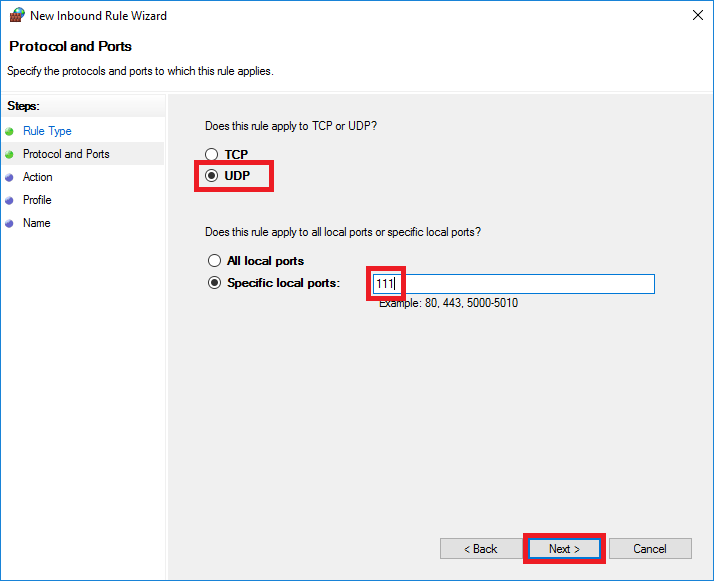
Step 5
Select 'Block the connection' and click 'Next'. On the next page, click 'Next' again.
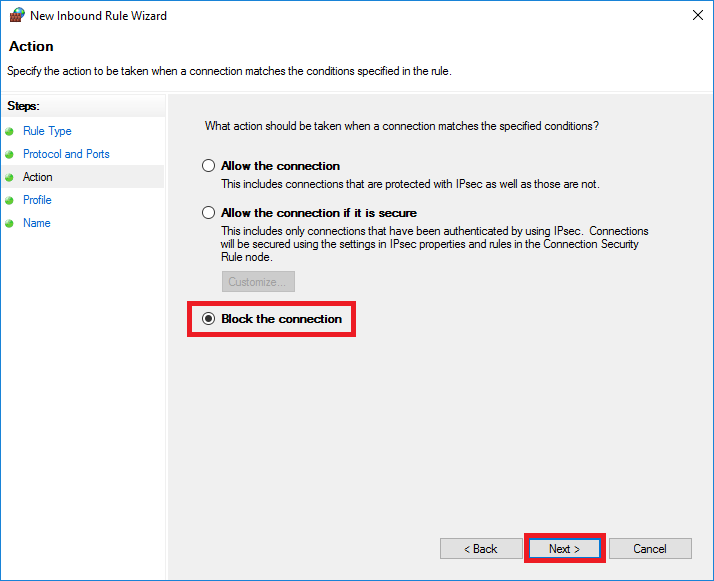
Step 6
Then, give your new rule a name and optionally a description.
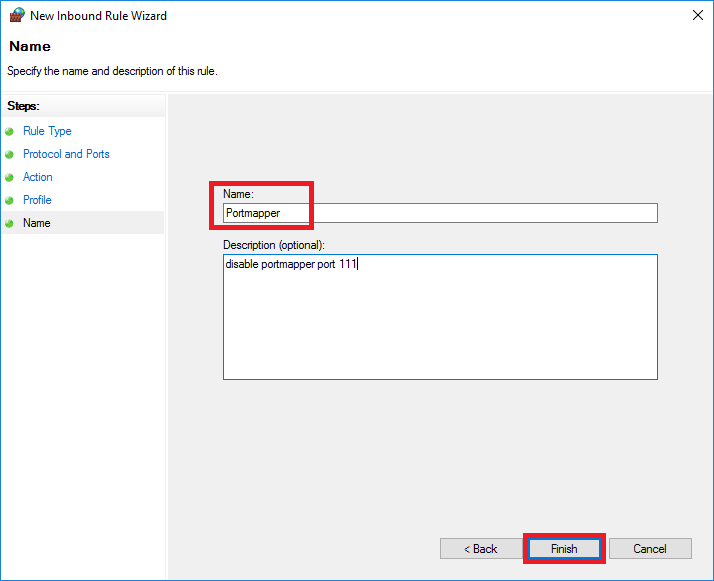
If you still want to make the service available locally, you can also set specific IP addresses in the whitelist for the properties of this rule.
Testing the portmapper service
If you use an OS with a terminal on your client computer (such as OS X, BSD or Linux), you can use 'rpcinfo' to check if a portmapper service is still active.
rpcinfo -p [IP ADDRESS] -T udp
Should you have any questions left regarding this article, do not hesitate to contact our support department. You can reach them via the ‘Contact Us’ button at the bottom of this page.




