On July 24, 2023, AMD released information about a critical vulnerability named 'Zenbleed' in all AMD Zen 2 processors. By exploiting this vulnerability, potentially protected information such as encryption keys and login details can be stolen from a CPU.
Thanks to the researcher who discovered the vulnerability, Tavis Ormandy, a micro-update and workaround were already available for the server versions of the AMD Zen 2 processors. We have therefore applied this immediately to our PerformanceVPS platform that uses these processors.
There is no micro-update available yet for the commercial AMD Zen 2 CPUs used in home computers and laptops. AMD indicates that micro-updates will become available for commercial CPUs between October and December.
In this tutorial, we therefore explain how to check if your computer/laptop uses a Zen 2 CPU and how to apply the workaround to protect yourself against the Zenbleed vulnerability.
This article does not apply to your VPS but applies to your home computer/laptop.
The Zenbleed vulnerability
The vulnerability is designated CVE-2023-20593 and is the result of a bug that under specific circumstances allows an attacker to obtain sensitive information from the CPU. The attacker does not need access to a home computer or laptop. An attack exploiting this vulnerability, for instance, can be executed from a website via JavaScript. The visiting of a website can as such be sufficient to retrieve data from your CPU.
On the website of the discoverer of this vulnerability, Tavis Ormandy, you will find a detailed explanation about the discovery, solution, and misuse of this vulnerability. As he puts it, the vulnerability boils down to:
"The bug works like this, first you have to activate something called the XMM Register Merge Optimization2, followed by a register renaming and a wrongly predicted vzeroupper. All of this must happen within a precise time window to work.
We now know that basic operations like strlen, memcpy and strcmp will use the vector registers - so we can effectively spy on those operations happening anywhere in the system! It doesn't matter whether they occur in other virtual machines, sandboxes, containers, processes, whatever!
This works because the register file is shared by everything on the same physical core. In fact, two hyperthreads even share the same physical register file."
List of affected Zen 2 CPUs
- AMD Ryzen 3000 Series Processors
- AMD Ryzen PRO 3000 Series Processors
- AMD Ryzen Threadripper 3000 Series Processors
- AMD Ryzen 4000 Series Processors with Radeon Graphics
- AMD Ryzen PRO 4000 Series Processors
- AMD Ryzen 5000 Series Processors with Radeon Graphics
- AMD Ryzen 7020 Series Processors with Radeon Graphics
- AMD EPYC Rome Processors
AMD Zen 2 CPUs are also used for the PS5, Xbox Series X & S, and Steam Deck. However, it is unclear at this moment whether these have also been affected by the Zenbleed vulnerability.
Check if your computer uses a Zen 2 CPU
If you are not sure what type of processor you are using, you can find this out within your operating system as follows:
Windows:
Press the Windows Start icon + R on your keyboard at the same time. The execute/run screen appears. Type the command 'dxdiag' and press 'OK' or the enter key.
The DirectX Diagnostic Tool window appears. Check here whether behind 'Processor' one of the processor types is listed from the previous paragraph. For an AMD 5000 series processor, for example, it would look something like: 'AMD Ryzen 5 5600X (6 CPUs) ~ 3.7 ghz'.
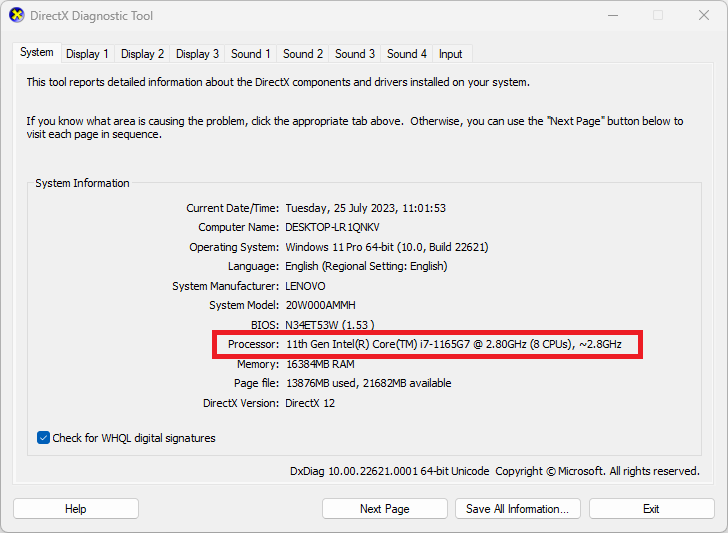
If you see a vulnerable processor here, proceed to the next paragraph.
Linux
Open a terminal and run the following command:
lscpu | grep "Model name"
The output will look something like this:
Model name: AMD Ryzen 5 5600 Six-Core processor
If you see a vulnerable processor here, proceed to the next paragraph.
Applying the workaround against the Zenbleed vulnerability on your CPU
First and foremost, we always recommend applying the micro-update on your computer if available. Until it is available, you can apply a workaround to protect your computer by setting the 'chicken bit'.
AMD indicates that the workaround may have an impact on the performance of your processor. However, they cannot specify under what circumstances and how much impact there is. However, you can later undo the workaround and apply the micro-update on your computer to remove any potential impact.
Windows:
We are still working on the instructions for Windows and will update this article as soon as possible.
Linux:
With each reboot, the workaround is undone. You could, for example, create a startup script to automatically apply the workaround in step 2 and apply the micro-update when it is available, and then remove your startup script. The micro-update will remain in effect after a reboot in due course.
- First, install the MSR-tools on your computer. These are necessary to apply the workaround:
Ubuntu/Debian:CentOS/AlmaLinux/Rocky Linux:sudo apt -y install msr-toolssudo dnf -y install msr-tools - Execute the following command(s) to apply the workaround:
Note: With each reboot, the workaround is undone. You could, for example, create a startup script to automatically apply the workaround and apply the micro-update when it becomes available. We'll document an instruction for this shortly as well.
wrmsr -a 0xc0011029 $(($(rdmsr -c 0xc0011029) | (1<<9)))




