Via the control panel you can enable or disable a number of web filters for your web hosting package. In this article we explain how to do this and briefly explain what each filter is for.
Log in to the control panel and click 'Shared Hosting' in the menu. Next, select your domain below 'Products'.
Click the 'Security' tab at the top, followed by 'Webfilters'.
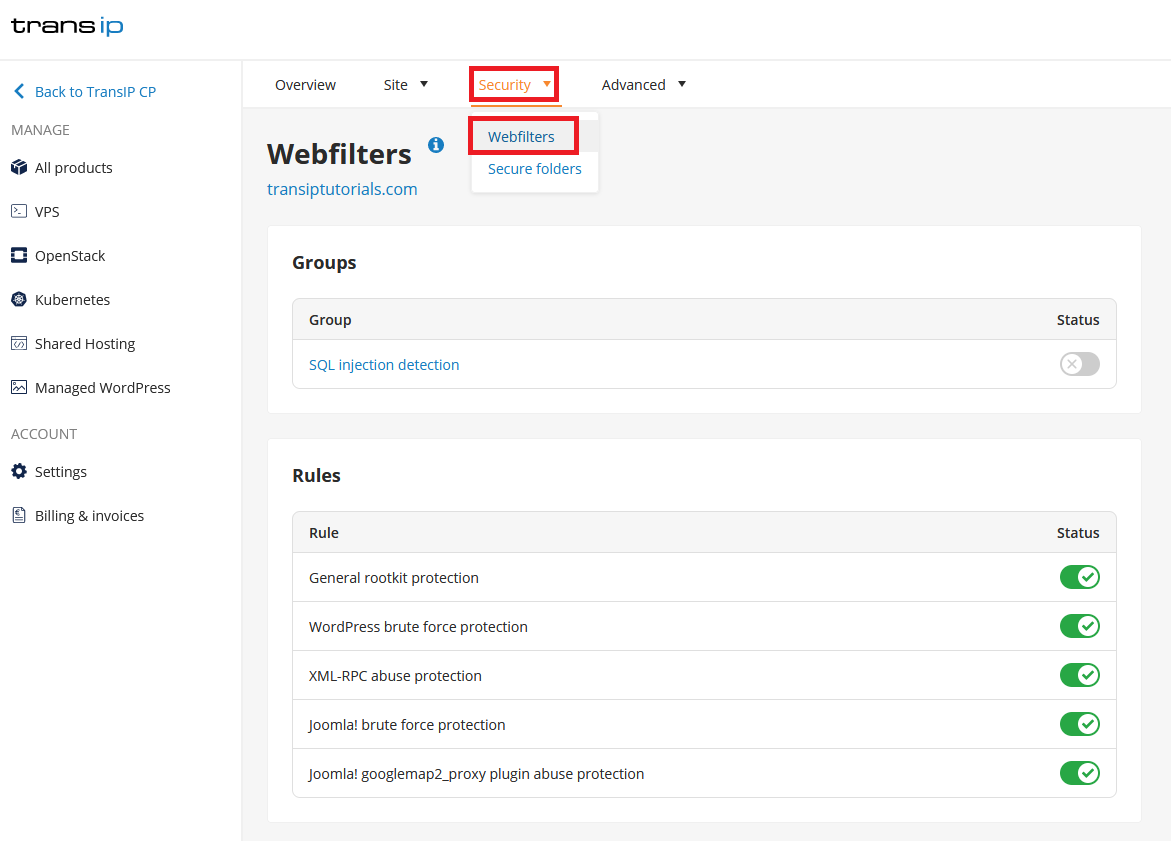
You can enable or disable the different filters by clicking the sliding button on the right side, below 'Status'. We will explain briefly what the different options mean.
Groups
SQL injection detection
SQL injection detection checks for a number of possible database attacks. Upon detection, the source of the attack is blocked. SQL injection detection checks the following attacks/injections:
- Blind SQL injection tests using sleep() or benchmark()
- MSSQL code execution and information gathering attempts
- MySQL and PostgreSQL stored procedure/function injections
- MySQL charset switch and MSSSQL DoS attempts
- MySQL UDF injection and other data/structure manipulation attempts
- PostgreSQL pg_sleep injection, waitfor delay attacks and database shutdown attempts
- SQL benchmark and sleep injection attempts including conditional queries
- Basic MongoDB SQL injection attempts
- Basic SQL injection. Common attack string for MySQL, Oracle and others
- Integer overflow attacks, these are taken from skipfish
Rules
Disable /xmlrpc.php access
xmlrpc.php is used by older versions of WordPress to connect to third party platforms. By disabling it you protect yourself against DDoS attacks via xmlrpc.php.
Disable /autodiscover/autodiscover.xml access
autodiscover.xml is used to automatically configure mail settings. Incorrectly configured mail software may cause repeated and unnecessary calls for the autodiscover.xml file. This can cause a load to the server. By disabling it you prevent this issue.
Disable /wp-includes/wlwmanifest.xml access
Disables wlwmanifest.xml (Windows Live Writer Manifest). Having this file enabled may cause bots to detect that you have WordPress installed. Once spotted, they may search for WordPress vulnerabilities.
Disable .git/ access
Disables access to a .git/ folder which could contain sensitive data.
General rootkit protection
General protection against rootkits. A rootkit is malware which tries to access your website/data.
WordPress brute force protection
Protection against brute force attacks on your WordPress website. Brute force attacks are automated attempts to guess for instance your password.
In addition to the obvious implications of comprimised credentials, unsuccesful attemtps are also not desirable, as they result in a large number of requests being made to your web hosting. This can make your website slower than you are used to.
If you try to log in multiple times with wrong login details, WordPress brute force protection may block your own IP temporarily. This will result in a 403 Forbidden error. You can check whether this is the case by logging in from a different IP address, for example via your phone's 4G/5G network.
XML-RPC abuse protection
Protection against brute force attacks via xmlrpc.php. xmlrpc.php is used by older versions of WordPress to connect to third party platforms.
Joomla! brute force protection
General protection for Joomla websites against brute force attacks.
Joomla! googlemap2_proxy plugin abuse protection
Protection against DDoS attacks which make use of a Google Maps plugin.




