Within a Windows domain/Active Directory environment, it is desirable to restrict access to remote desktop servers to specific users and groups. Microsoft offers various options with which you can restrict remote desktop access, of which you will find an overview in our article 'restricting Remote Desktop access'.
In this tutorial, we will show you how to use group policies to prohibit users and/or groups from accessing remote desktop in an Active Directory environment.
Step 1
Connect via remote desktop or the VPS console as domain administrator to your remote desktop server.
Step 2
Click the Windows Start button and search for 'gpedit'. Click 'Edit group policy' in the results.
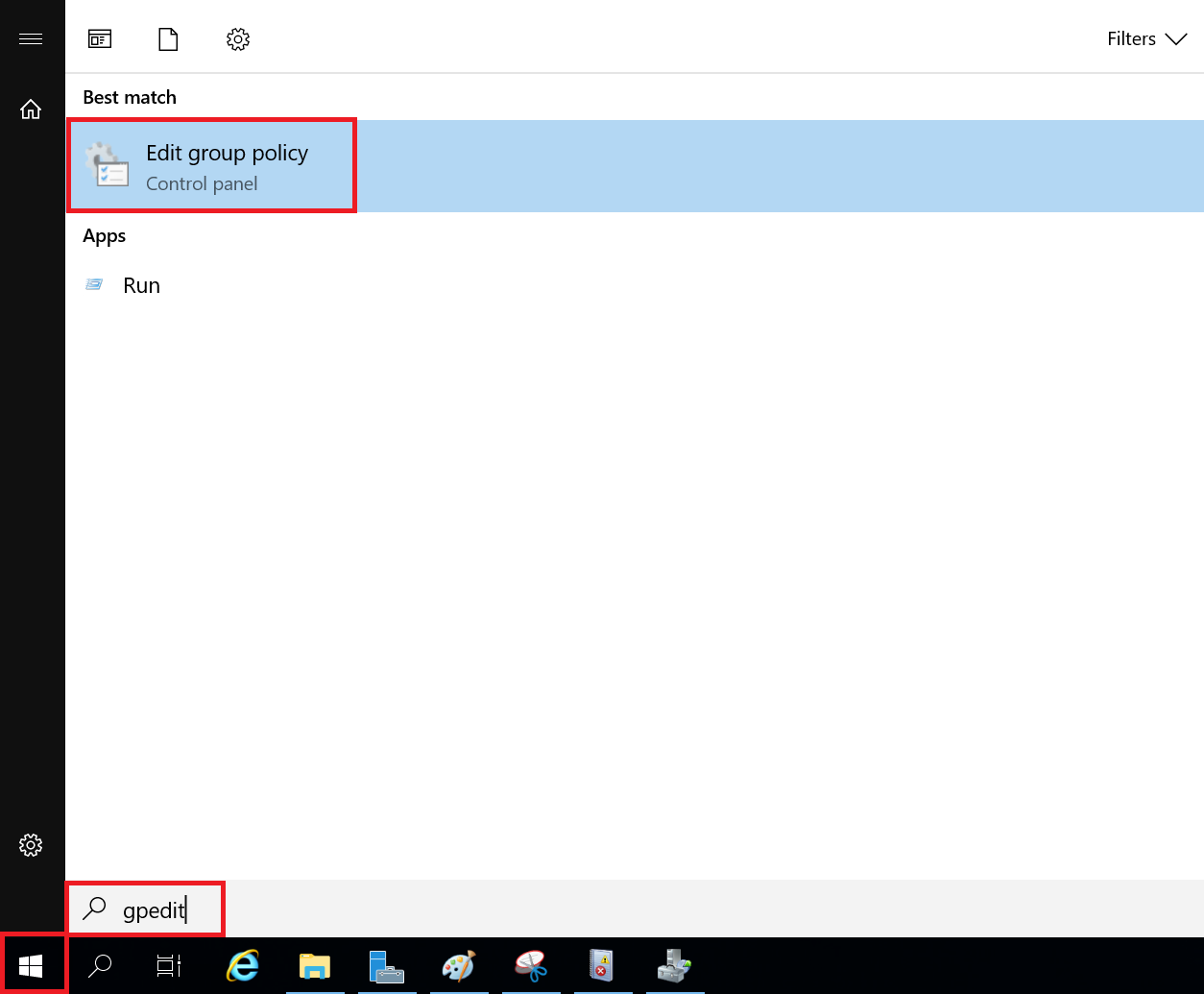
Step 3
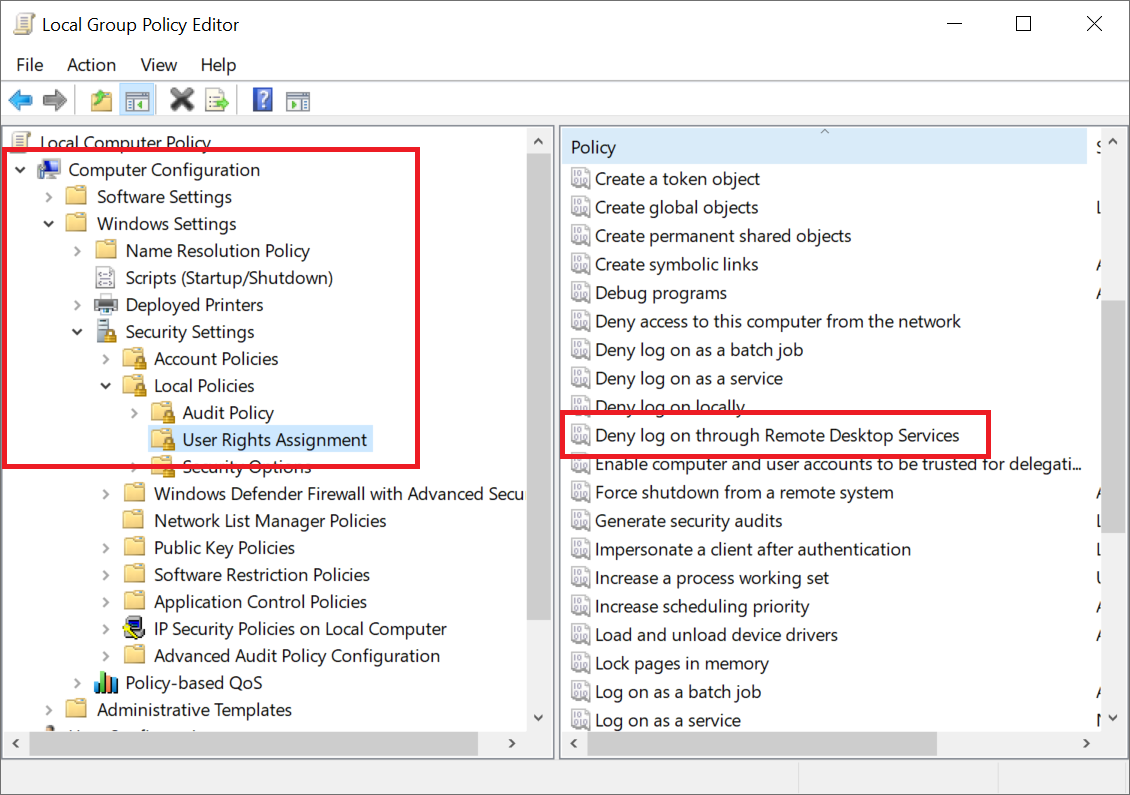
In the left menu, expand the following options: Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Assignment.
Then double click 'Deny logon through Remote Desktop Services'.
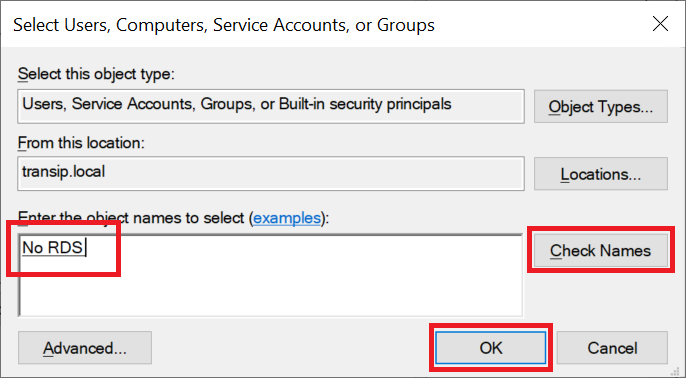
Step 4
Click 'Add User or Group...', search for the user or group you want to deny remote desktop access to, then click 'OK'. The easiest way is to use a group and add users to it who are not allowed to access Remote Desktop. Have you not yet created a group for this? Then do so first with the help of our Active Directory User and Group management manual.
Click 'Apply' and 'OK' to apply the change.
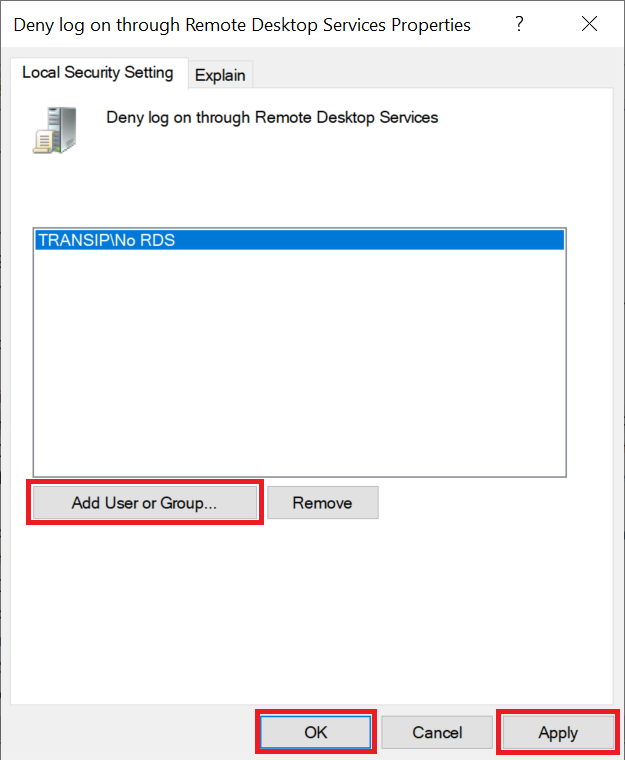
Step 5
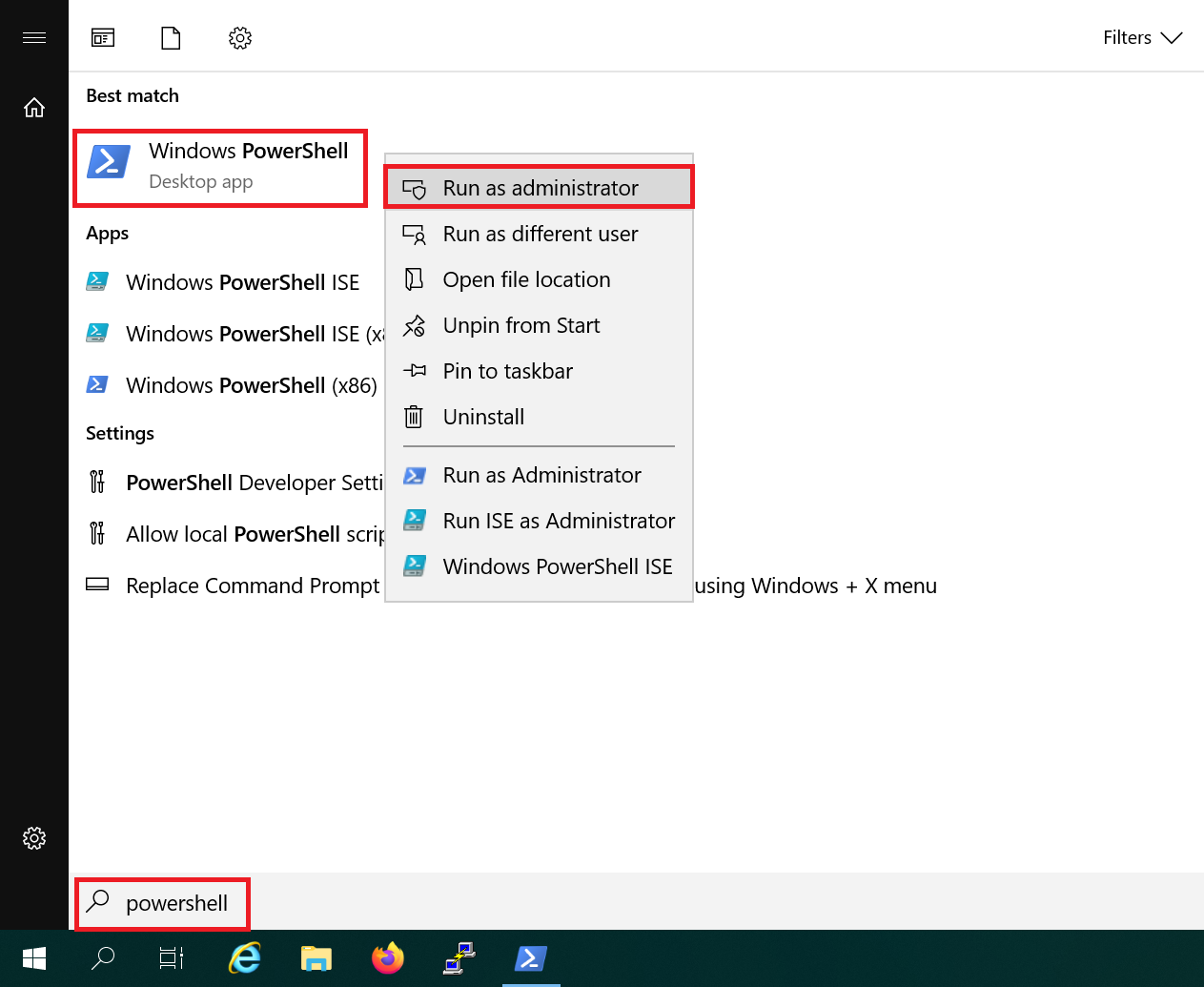
Press the Windows Start button, type 'Powershell' and right click Windows Powershell and select 'Run as administrator'.
Step 6
Use the following command to apply the policy change:
gpupdate /force
Group policy updates are periodically made to your servers. To apply this change immediately, repeat steps 5 and 6 on the servers on which you want to restrict RDP access.
This brings us to the end of this guide on restricting RDS access via group policies.




